US & Canada Confirm: China-Linked Hackers Stole Massive Login Data via VMware
Look, I hate to be the guy who ruins your morning coffee with more "doom and gloom" cyber news. We’re all tired of it. Another day, another breach, another apology letter from a CEO offering you one year of free credit monitoring.
But this one? This is different.
On Thursday (December 4), and reiterated over the weekend by the Times of India, cybersecurity heavyweights from the US (CISA, NSA, FBI) and Canada (CCCS) dropped a joint advisory that should make every IT admin sweat.
They confirmed that China-linked hackers—specifically a state-sponsored group—have been using a nasty piece of malware called "Brickstorm" to pull off what essentially amounts to a digital heist of the highest order. They didn't just break in; they stole the keys, the blueprints, and the alarm codes.
We’re talking about the theft of massive login data caches from government and IT entities, maintained over a period of months. If you work in tech, especially in India’s massive IT services sector which runs on the very software targeted, you need to pay attention.
What Actually Happened?
The agencies identified a specific campaign where hackers targeted VMware vSphere.
For the uninitiated, vSphere is the bread and butter of enterprise IT. It’s the software that allows companies to run virtual machines (VMs)—essentially digital computers inside physical computers. It’s used by everyone from Fortune 500 banks to the government agency processing your tax return.
The Attack Vector: The hackers deployed "Brickstorm" to target these vSphere environments. But here is the kicker: they didn't just steal a few files. They stole cloned virtual machine snapshots.
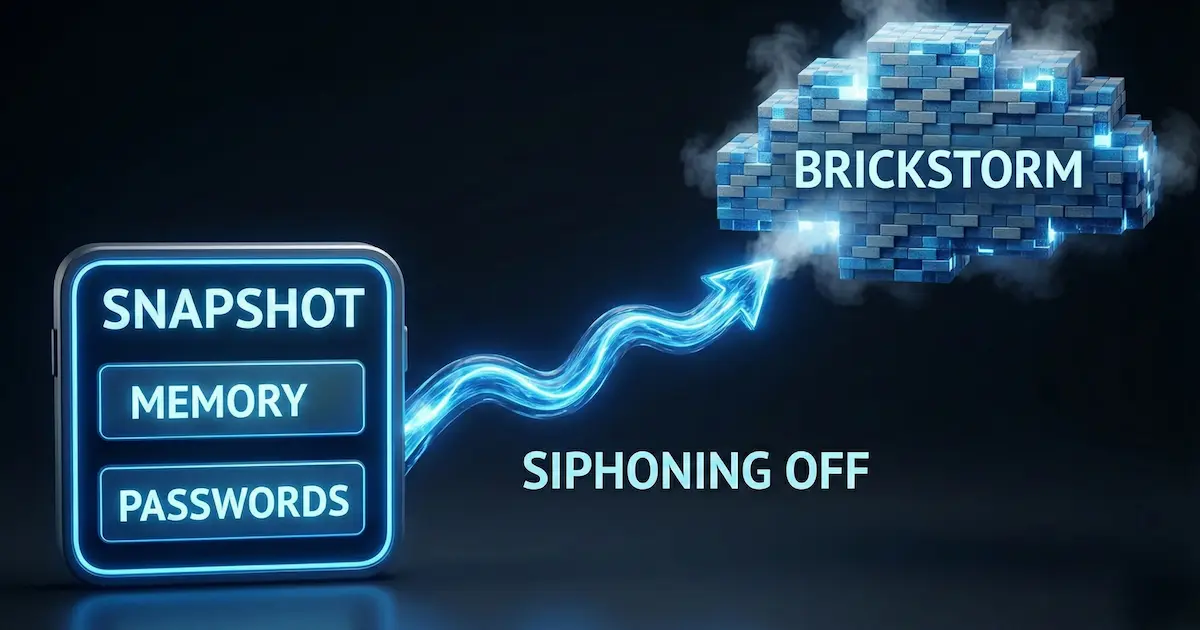
Why is that terrifying?
A VM snapshot is a frozen moment in time of a computer. It contains everything on the hard drive, sure, but it also captures the active memory (RAM).
What lives in RAM? Your unencrypted passwords.
What else? Your active session tokens.
The Result: The hackers didn't need to crack your password. They just took a photo of it while you were typing it.
The Timeline of Terror
This wasn't a "smash and grab." It was a "move in and redecorate."
The advisory cited one specific case where attackers used Brickstorm to penetrate a company in April 2024 and maintained access through at least September 3, 2025.
That is nearly 18 months of persistence.
Imagine someone living in your attic for a year and a half, listening to every conversation, noting down every PIN code, and you only find out because the neighbor (CISA) saw them peek through the blinds.
How "Brickstorm" Works (The Technical Grit)
If you’re a developer or sysadmin, here is the under-the-hood breakdown. If you’re not, skip to the "So What" section.
- Infiltration: The actors likely used known vulnerabilities or stolen credentials (ironic, right?) to get initial access to the vSphere environment.
- The Payload: They deployed Brickstorm, a sophisticated backdoor.
- The Theft: They targeted the vmsn and vmem files (snapshot and memory files).
- Credential Dumping: By analyzing these memory dumps offline, they extracted cleartext credentials for domain admins.
- Persistence: They created "rogue VMs"—hidden virtual machines running on the victim's own hardware—to launch further attacks or exfiltrate data without triggering standard antivirus alarms.
Expert Note: The Chinese Embassy in Washington, via spokesperson Liu Pengyu, has denied these allegations, calling them "irresponsible assertions" without factual evidence. This is standard diplomatic protocol, but the CISA/NSA technical receipts (YARA rules and IOCs) tell a very specific story.
So What? (The India & Global Impact)
You might be sitting in Bengaluru or Hyderabad thinking, "This is a US/Canada advisory. Why do I care?"
- The "Back Office" Reality India is the world's back office. A massive chunk of the Global 2000's IT infrastructure is managed from tech parks in India. If a US client is hit via VMware, the Indian service provider managing that stack is largely involved in the cleanup—or worse, might have been the entry point via a shared credential.
- Ubiquity of VMware VMware vSphere is the standard in Indian data centers. Whether it's banking (RBI regulated entities), telecom, or government cloud services, vSphere is the engine. If "Brickstorm" is in the wild, Indian networks are just as vulnerable as American ones.
- The Sabotage Risk Madhu Gottumukkala, the acting director of CISA, didn't mince words. He said these hackers are embedding themselves for "potential sabotage." This isn't just espionage (stealing secrets); it's pre-positioning to shut things down if geopolitical tensions rise.
Risks & Unknowns
There is still a lot we don't know, and that's the scary part.
- Total Victim Count: CISA Executive Assistant Director Nick Andersen declined to share the total number of organizations hit. "Unnamed government entities" is vague and unsettling.
- The Broadcom Factor: Broadcom (who owns VMware) says they are aware and urging patches. But are there zero-day vulnerabilities involved that haven't been patched yet? The advisory focuses on "known vulnerabilities," but the sophistication of Brickstorm suggests high-level tradecraft.
What Experts Disagree On
Attribution Confidence: While the US and Canada are 100% sure this is China ("Volt Typhoon" and "Salt Typhoon" are related groups often cited), some independent researchers argue that attribution based solely on malware signatures can be tricky. However, given the scale and the targets (critical infra), the state-sponsored label is widely accepted by the community.
The "fix" timeline: Some experts believe patching now is enough. Others argue that if they were in your system for 18 months, you can't just patch. You might need to "burn it down"—wipe the hardware and rebuild from scratch—because the trust in that environment is gone.
The Verdict: What You Need To Do NOW
If you manage a server, or know the guy who does, here is the checklist. Do not wait for Monday.
- Check the Logs: Look for unusual snapshot activity. If you see snapshots being created and deleted at weird hours (3 AM IST), that’s a red flag.
- Hunt for "Brickstorm": CISA has released YARA rules (code snippets used to identify malware). Run them.
- Patch vSphere: Broadcom has updates. Apply them. Yesterday.
- Assume Compromise: If you find evidence of Brickstorm, do not just delete the file. Assume they have your admin passwords. Reset all credentials, not just the ones you think were stolen.
My Take: We are moving into an era where "password theft" doesn't mean phishing your aunt on Facebook. It means nation-states scraping the RAM of the servers that run the internet.
Stay paranoid, folks.
