The Breach Nobody Wants to Talk About
Here's a scenario that probably keeps millions of people up at night: your email, your viewing habits, your location—all tied to the adult content you've consumed—suddenly sitting in the hands of cybercriminals.
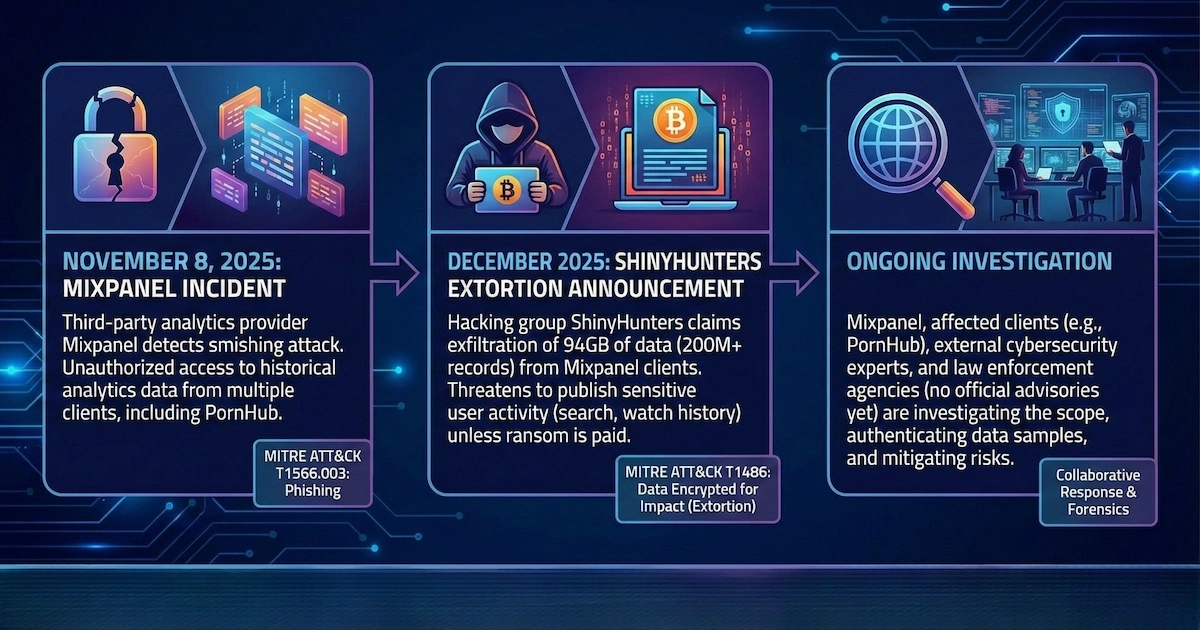
That nightmare became reality in December 2025 when the ransomware group Scattered Lapsus$ Hunters, which includes members of the notorious ShinyHunters gang, announced they had obtained approximately 94 GB of data containing more than 200 million analytics records tied to Pornhub Premium activity. The breach allegedly exposed email addresses, locations, activity types, video URLs, video names, keywords associated with watched content, and timestamps of when users accessed specific material.
The adult platform has confirmed it was among several companies affected by a security incident at Mixpanel, a third-party analytics provider. The site stressed this wasn't a breach of its own systems and that passwords, payment details, and government IDs were not compromised. Mixpanel, however, disputes that the stolen data originated from its November 2025 security incident, claiming the data was last accessed by a legitimate employee account at the platform's parent company, Aylo, back in 2023.
The finger-pointing between vendors matters less than the cold reality facing affected users: highly sensitive behavioral data is now in criminal hands.
Why This Breach Is Particularly Dangerous
Most data breaches expose the usual suspects—names, emails, maybe passwords. This one carries a different kind of payload.
The exposed information reportedly includes not just that someone visited an adult site, but exactly what they watched, when they watched it, and what keywords were associated with that content. For context, similar breaches of adult platforms in the past—like the FriendFinder Networks hack that exposed 412 million accounts or the Ashley Madison breach that exposed 30 million users—led to documented cases of blackmail, destroyed marriages, and, tragically, suicides.
Sextortion scams have already surged 137% in the United States during 2025, according to Avast's threat intelligence data. Criminals now combine leaked personal data with AI-generated deepfakes and Google Street View images of victims' homes to create terrifyingly convincing extortion messages. This breach hands them a new arsenal.
The emotional leverage here is obvious. Someone threatening to expose your Netflix viewing history is annoying. Someone threatening to expose your adult content preferences to your employer, spouse, or religious community is devastating—even if their threats are ultimately empty.
What Was Actually Exposed
Based on available reporting from TechCrunch and BleepingComputer, the stolen data sample included:
- Email addresses linked to premium accounts
- Geographic location data
- Activity types (videos watched, channels followed)
- Video URLs and names
- Associated keywords/tags
- Timestamps of activity
The affected platform has explicitly confirmed that passwords, payment details, and government identification were NOT exposed in this incident. This is important context—your credit card isn't directly at risk from this specific breach.
Your 7-Step Identity Protection Playbook
Step 1: Check If You're Compromised
Before panicking, determine your actual exposure level.
Use Have I Been Pwned (haveibeenpwned.com) to search your email addresses. This free service, created by security researcher Troy Hunt, indexes over 12 billion records from known breaches. Enter your email—if it appears in breach databases once this data is added, you'll know immediately.
Enable breach notifications on the same site. You'll receive an automatic alert if your email appears in future database dumps.
Pro tip: The breach data may not immediately appear in public breach databases because the hackers are currently using it for extortion, not public release. Consider this step ongoing surveillance rather than a one-time check.
Step 2: Freeze Your Credit Immediately
Even though payment data wasn't directly exposed in this breach, your email and location data can be combined with information from other breaches to enable identity theft.
A credit freeze prevents anyone—including you—from opening new credit accounts until you lift it. It's free, it doesn't affect your credit score, and it takes about 10 minutes to set up with all three bureaus.
Contact each bureau directly:
- Equifax: equifax.com/personal/credit-report-services/credit-freeze or call (888) 298-0045
- Experian: experian.com/freeze or call (888) 397-3742
- TransUnion: transunion.com/credit-freeze or call (888) 909-8872
You must freeze with all three separately—they don't automatically notify each other. When you need to apply for credit later, you can lift the freeze temporarily at the specific bureau your lender uses.
Step 3: Add a Fraud Alert (Use Both)
A fraud alert tells creditors to verify your identity before issuing credit in your name. Unlike a freeze, you only need to contact one bureau—they're required to notify the others.
Three alert types exist:
Alert Type | Duration | Who Qualifies |
Initial Fraud Alert | 1 year (renewable) | Anyone concerned about identity theft |
Extended Fraud Alert | 7 years | Verified identity theft victims with FTC report |
Active Duty Alert | 1 year | Military personnel on deployment |
Fraud alerts and credit freezes can work together. The freeze blocks access; the alert adds verification steps when you temporarily lift that freeze.
Step 4: Prepare for Sextortion Attempts
Here's what to expect: emails or messages claiming the sender has your "private videos" and threatening to release them unless you pay in Bitcoin.
The critical rules:
- Never pay. According to Digital Forensics Corp's 2025 sextortion study, 40% of victims who paid received daily threats afterward. Payment proves you're a viable target.
- Never respond. Any engagement confirms your email is active.
- Don't open attachments or PDFs. They may contain malware.
Most sextortion emails are mass-produced scams using old leaked passwords to create an illusion of access. The scammer probably doesn't have any actual footage of you—they're betting that guilt and fear will drive payment.
If you receive such a message:
- Take a screenshot for evidence
- Report to the FBI's Internet Crime Complaint Center (IC3) at ic3.gov
- Report to the FTC at reportfraud.ftc.gov
- Block the sender and move on
Step 5: Change Passwords and Enable 2FA
If you reused your account password anywhere else—stop reading this and go change those passwords immediately.
Password hygiene fundamentals:
- Use a unique password for every account
- Minimum 16 characters with mixed case, numbers, and symbols
- Use a password manager (1Password, Bitwarden, Dashlane) to generate and store them
Enable two-factor authentication (2FA) on every account that supports it, prioritizing:
- Email accounts (the skeleton key to your digital life)
- Financial accounts (banking, investment, crypto)
- Social media (often used for recovery)
Prefer authenticator apps (Google Authenticator, Authy, Microsoft Authenticator) over SMS-based 2FA when possible. SIM-swapping attacks can intercept text-message codes.
Step 6: Monitor Financial Accounts Aggressively
Set up transaction alerts on all bank accounts and credit cards. Most financial institutions allow you to receive instant notifications for any transaction above ₹0 / $0.
Review your accounts for:
- Small test charges (criminals often verify stolen cards with tiny purchases)
- Unfamiliar recurring subscriptions
- Address changes you didn't authorize
- New authorized users added to accounts
Step 7: Document Everything
If identity theft does occur, your recovery will be smoother with documentation.
- Save copies of any suspicious emails or extortion attempts
- Screenshot any fraudulent transactions before reporting them
- Request and review your free annual credit reports from all three bureaus at annualcreditreport.com
- If fraud occurs, file an identity theft report at IdentityTheft.gov—this generates a personalized recovery plan and creates official documentation for creditors

What Experts Are Still Debating
The source of the breach remains disputed. The affected platform blames Mixpanel's November 2025 security incident. Mixpanel insists its systems weren't the source and that the parent company last accessed the data in 2023—implying the leak may have come from Aylo's own environment.
The extortion timeline is unclear. The hackers haven't publicly released the full database yet. Whether they're negotiating with Aylo, waiting for maximum leverage, or planning a broader distribution remains unknown.
Long-term exposure risk is uncertain. Unlike password leaks, viewing history can't be "changed." If this data eventually surfaces publicly, affected users may face recurring privacy risks for years.
The Uncomfortable Reality
No set of security measures can un-leak data that's already out. If your email was linked to a premium account on the affected platform and that data is now in criminal hands, the bell cannot be unrung.
What you can control is how prepared you are for the consequences. Freezing your credit won't prevent embarrassment, but it will prevent someone from opening a credit card in your name. Ignoring sextortion emails won't erase your viewing history, but paying the extortionists will only invite more demands.
The breaches will keep coming. This year alone has seen compromises affecting OpenAI, SoundCloud, 700Credit, and countless others—often from the same attack vectors targeting third-party analytics providers. Your best defense is assuming your data is already compromised and building systems that limit the damage.
We'll update this guide if the platform, Mixpanel, or law enforcement releases additional information about the scope of exposure or official victim notification processes.
